GitHub security Alerts
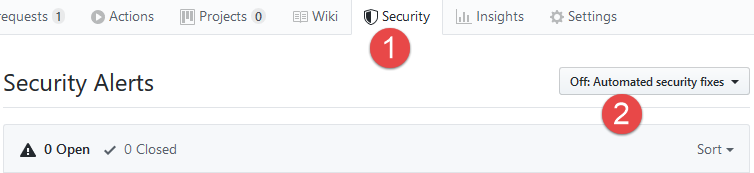
I really love everything about security and I’m really intrigued by GitHub security tab that is now present on you repository. In your project usually it is disabled by default.
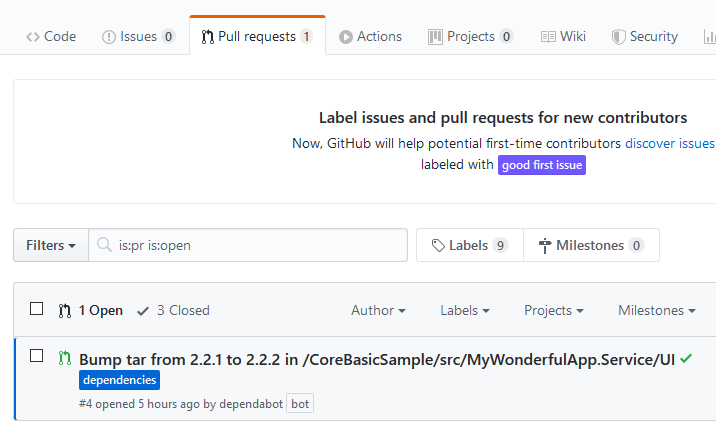
Figure 1: GitHub Security tab on your repository
If you enable it you start receiving suggestion based on code that you check in on the repository , as an example, GitHub will scan your npm packages source to find dependencies with libraries that are insecure.
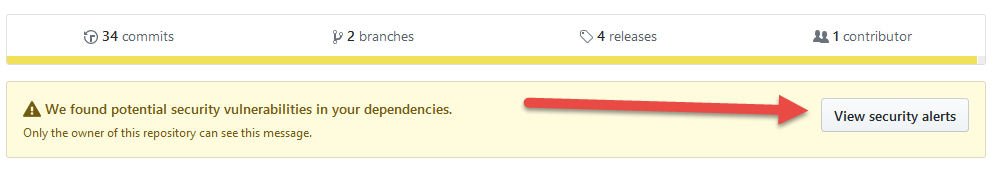
When GitHub found something that require your attention, it will put a nice warning header on your project, so the alert cannot really pass unnoticed.
Figure 2: Security alert warning banner
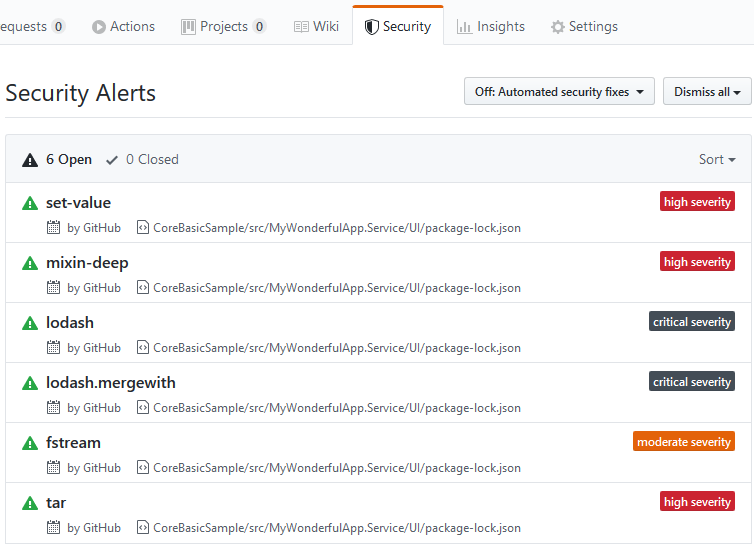
If you go to the security tab you got a detailed list of the analysis, so you can put a remediation plan in motion, or you can simply dismiss if you believe that you can live with them.
Figure 3: Summary of security issues for the repository
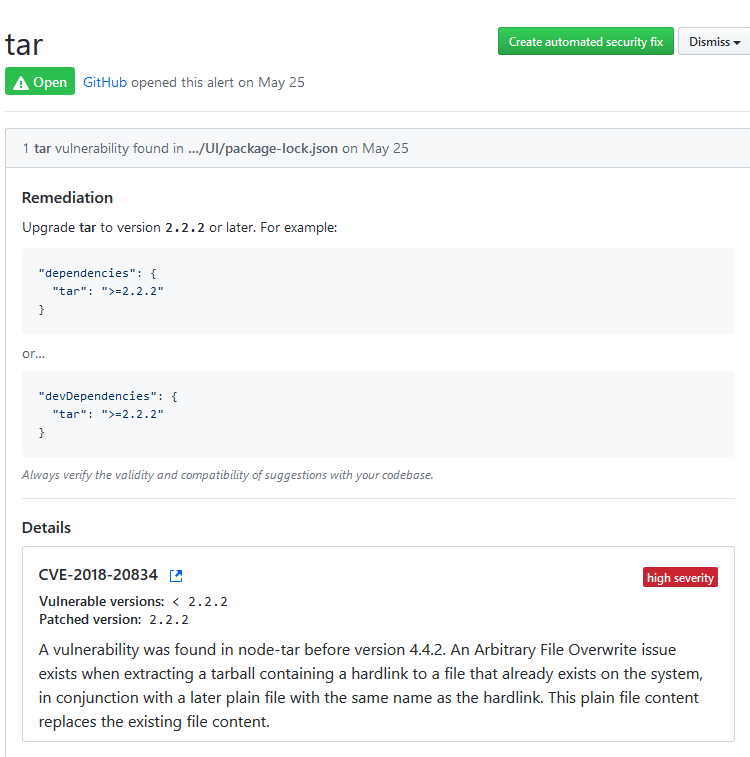
Clearly you can click on any issue to have a detailed description of the vulnerability, so you can decide if you are going to fix it or simple dismiss because that issue is not relevant to you or you cannot in anyway bypass the problem.
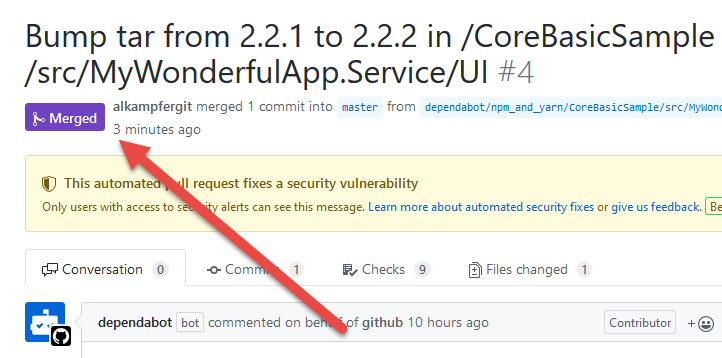
Figure 4: Detailed report of security issue
If you noticed in Figure 4 , you have also a nice button “Create Automated Security Fix” in the upper right part of the page, this means that not only GitHub is telling me where the vulnerability is, it sometimes can fix the code for me. Pressing the button will simply create a new Pull Request to fix that error, how nice.
Figure 5: Pull request with the fix for the security issue
In this specific situation it is simply a vulnerable package that is donwloaded by npm install, the change is simply bumping a library to a version that removed this vulnerability.
Actually GitHub perform a security scan on project dependencies and can present a remediation simply with nice pull requests
Using Pull request is really nice, really in the spirit of GitHub. The overall experience is really nice, the only annoying stuff is that actually the analysis seems to be done on master branch and proposed solution creates pull requests for master branch. While this is perfectly fine, the only problem I have is that, closing that pull request from the UI, it will merge this commit on the master branch, effectively bypassing GitFlow flow.
Since I’m a big fan of command line, I prefer to close that Pull request manually, so I simply issue a fetch, identify the new branch (it has annoying long name ![]() ) and simply checkout it as an hotfix branch
) and simply checkout it as an hotfix branch
| |
With this commands I simply checkout the remote branch as hotfix/0.3.1, so I can simply issue a git flow hotfix finish and pushing everything back to the repository. > If you have a specific flow for hotfixes, like GitFlow, it is quite easy closing Pull Requests locally, following your process, GitHub will automatically detect that the PR is closed after the push.
Now branch is correctly merged
Figure 6: Pull request manually merged.
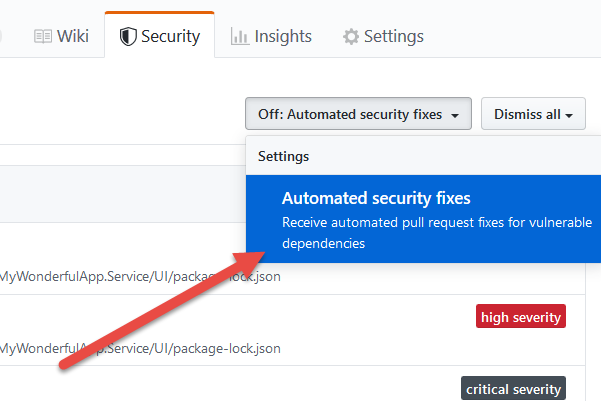
If you really like this process, you can simply ask GitHub to automatically create pull requests without your intervention. As soon as a security fix is present, a PR will be created.
Figure 7: You can ask to receive automated pull request for all vulnerabilities
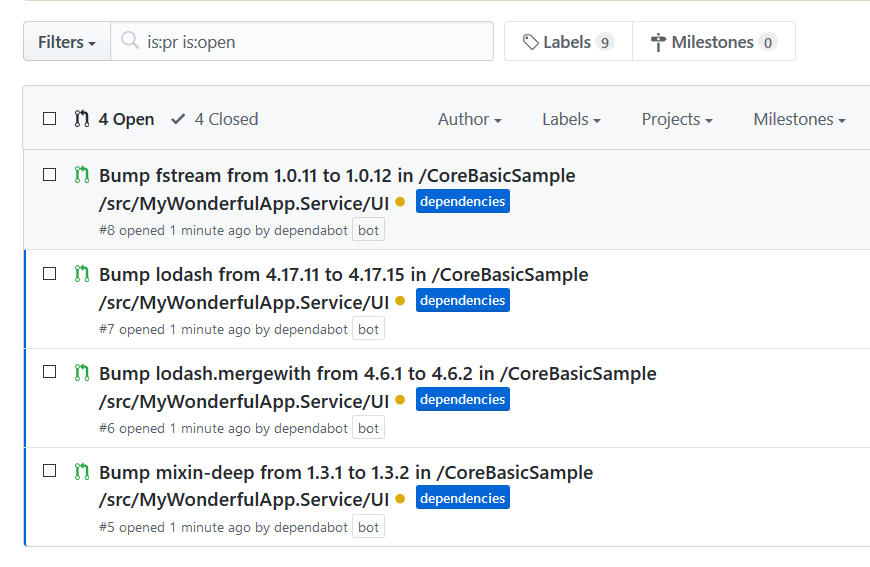
Et voilà, it is raining pull requests
Figure 8: A series of Pull requests made to resolve security risks
This raise another little issue, we have a single PR for each vulnerability, so, if I want to apply all of them in a unique big hotfix, I only need to manually start the hotfix, then fetch all those branches from the repo and finally cherry-pick all the commits. This operation is easy because each Pull Request contains a single commit that fixes a single vulnerability issue. Sequence of command is:
| |
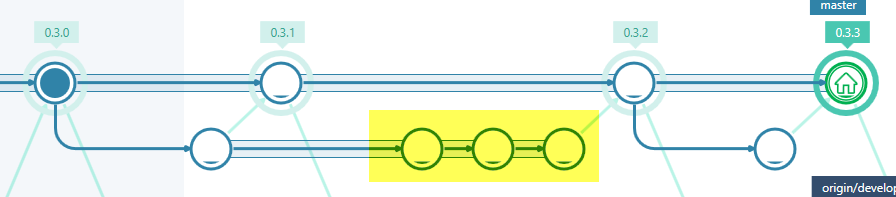
Final result is an hotfix resulted from cherry-picking of three distinct PR.
Figure 9: Three of pull requests were closed using simple cherry-pick
GitHub is really good in understanding that I’ve cherry-picked all commits in yellow from pull requests, because all pull requests were automatically closed after the push. 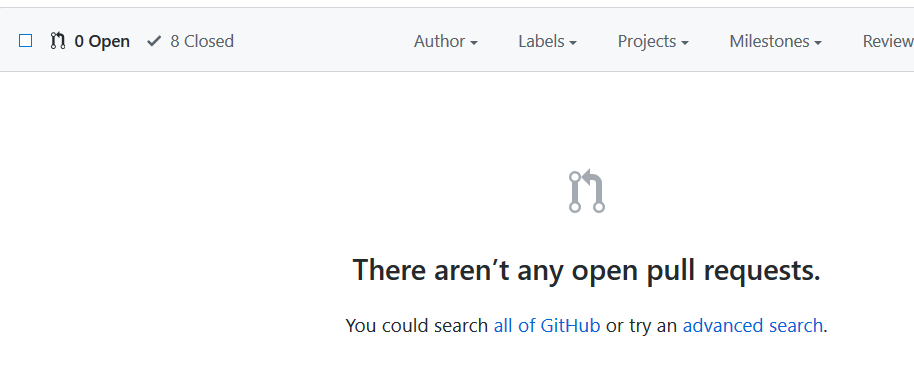
Figure 10: My pull requests are correctly closed even if I cherry-picked all commits manually.
Actually this functionality is really nice, in this simple repository I have really few lines of code but it helped me revealing some npm dependencies with vulnerabilities and, most important, it gave me the solution so I can immediately put a remediation in place.
Gian Maria.