Use the right Azure Service Endpoint in build vNext
Build vNext has a task dedicated to uploading files in azure blob , as you can see from Figure 1: 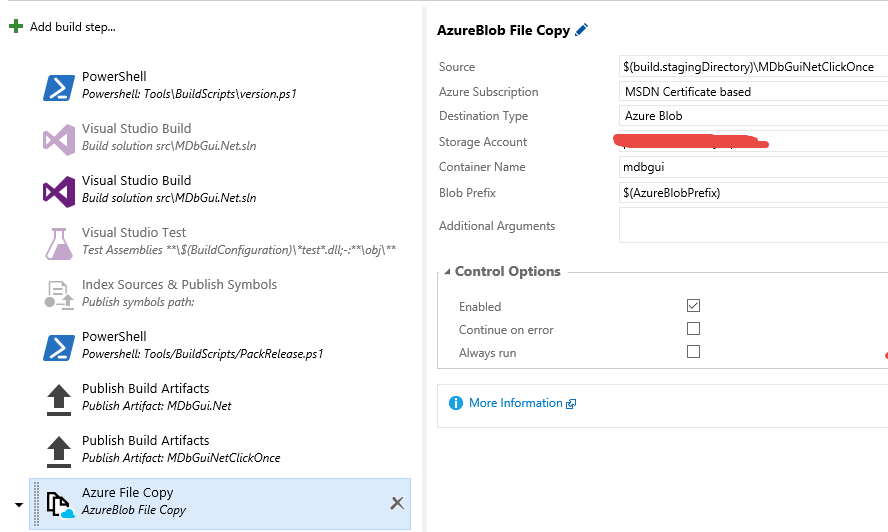
Figure 1: Azure File Copy task configured in a vNext build
The nice parte is the Azure Subscription setting, that allows to choose one of the Azure endpoint configured for the project. Using service endpoint, you can ask to the person that has password/keys for Azure Account to configure an endpoint. Once it is configured it can be used by team members with sufficient right to access it, without requiring them to know password or token or whatever else.
Thanks to Services Endpoints you can allow member of the team to create builds that can interact with Azure Accounts without giving them any password or token
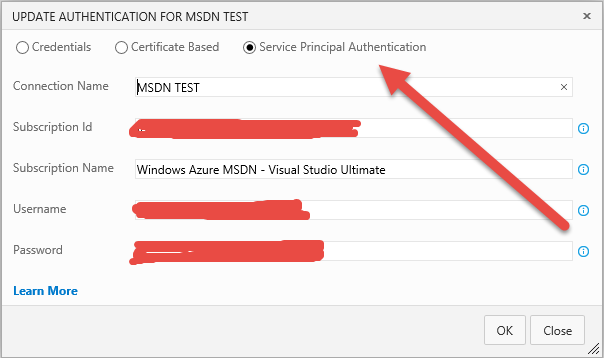
If you look around you find a nice blog post that explain how to connect your VSTS account using a service principal.
Figure 2: Configure a service endpoint for Azure with Service Principal Authentication
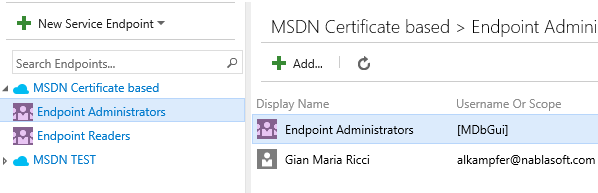
Another really interesting aspect of Service Endpoints, is the ability to choose people that can administer the account and people that can use the endpoint, thus giving you full security on who can do what.
Figure 3: You can manage security for each Service Endpoint configured
Finally, using Service Endpoint you have a centralized way to manage accessing your Azure Subscription Resources , if for some reason a subscription should be removed and not used anymore, you can simply remove the endpoint. This is a better approach than having data and password or token scattered all over the VSTS account (builds, etc).
I’ve followed all the steps in the article to connect your VSTS account using a service principal, but when it is time to execute the Azure File Copy action, I got a strange error.
| |
This error is really strange because the first error line told me:
** The subscription id xxxxxx-xxxxxx-xxxxxx-xxxxxxxxxxxxx doesn’t exist. This cannot be the real error, because I’m really sure that my Azure Subscription is active and it is working everywere else. Thanks to the help of Roopesh Nair, I was able to find my mistake. It turns out that the Storage Account I’m trying to access is an old one created with Azure Classic Mode, and it is not accessible with Service Principal. **A Service Endpoint using Service Principal can manage only Azure Resource Manager based entities.
Shame on me :) because I was aware of this limitation, but for some reason I completely forgot it this time.
Another sign of the problem is the error line telling me: Storage account xxxxxxxxx not found, that should ring a warning bell about the** script not being able to find that specific resource, because it is created with classic mode **.
The solution is simple, I could use a Blob Storage created with Azure Resource Manager, or I can configure another Service Endpoint, this time based on a management certificate. The second option is preferrable, because** having two Service Endpoint, one configured with Service Principal and the other configured with Certificate allows me to manage all type of Azure Resources **.
Configure an endpoint with certificate is really simple, you should only copy data from the management certificate inside the Endpoint Configuration and you are ready to go.
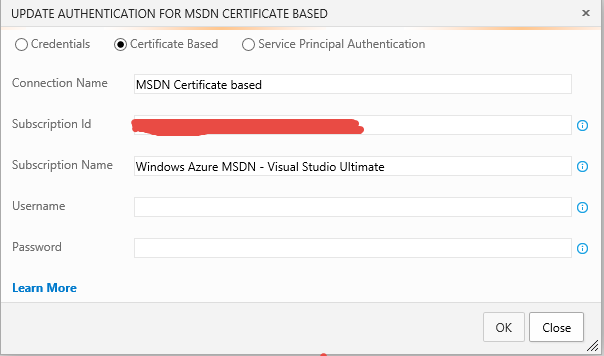 ** Figure 4: **Configure an Endpoint based on Certificate
** Figure 4: **Configure an Endpoint based on Certificate
Now my build task Azure File Copy works as expected and I can choose the right Service Endpoint based on what type of resource I should access (Classic or ARM)
Gian Maria